 It seems like we may be closing in on the total size of Adobe’s password security breach, and it’s big. Really big.
It seems like we may be closing in on the total size of Adobe’s password security breach, and it’s big. Really big.
According to a report by Paul Ducklin at Sophos’s Naked Security blog, the breach includes more than 150 million usernames and encrypted passwords, alongside plaintext password hints for those accounts that have them set. Adobe is maintaining its claim that only 38 million of those records belong to active users.
Wiebke Lips, a Senior Manager for Corporate Communications at Adobe said in an email that it is likely that hackers also acquired “many invalid Adobe IDs, inactive Adobe IDs, Adobe IDs with invalid encrypted passwords, and test account data,” which may explain the large total number of Adobe IDs and passwords in the database. The company is still investigating how many of those accounts were involved in the breach.
Lips also said that Adobe has reset all of the passwords for affected accounts with valid passwords, whether they are active or not.
The hits don’t stop there, though. According to Sophos, there are a couple key problems with the way Adobe’s password file was set up: the company used an encryption scheme which would allow an attacker who got a hold of the database’s encryption key to decrypt the entire database, revealing all of the passwords at once.
In addition, the database was encrypted in such a way that the same password input would lead to the same encrypted text, so, for example, the password “qwerty” translates to “e5d8efed9088db0b” in Adobe’s database. Moreover, because of how the database is set up, it’s also possible to determine how many characters are in a given password by analyzing the ciphertext.
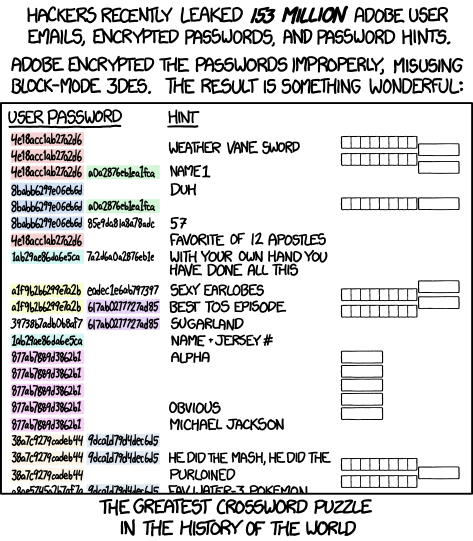
Compounding that, all of the password hints in the database are stored in plaintext, which means that the entire file amounts to what author Randall Munroe is calling “The greatest crossword puzzle in the history of the world.”
Lips confirmed Sophos’s assertions that the database was indeed encrypted with Triple DES and that if an attacker managed to get a hold of the database’s encryption key, it would be possible for them to decrypt the millions of passwords into plaintext all at once.
The good news, as minor as it may be, is that at the time of the attack, Adobe was already using a different scheme for protecting its primary password database. Lips said that for more than a year, the company has been salting passwords and hashing them using SHA-256, an algorithm that does a much better job of disguising password input. The Adobe password system involved in the attack was a backup system that was “designated to be decommissioned,” Lips said in an email.
It’s also worth noting that the database does not include the 2.9 million encrypted credit and debit card numbers that Adobe says were also taken in the attack. Those numbers were stored in a separate database, and according to Lips, they were encrypted with “a third-party appliance, which performs the encryption and manages the encryption keys.”
While Adobe says that it has contacted everyone affected by the attack, LastPass has created a tool that checks your email to see if the email associated with your Adobe ID is among those accounts included in the database. While the company hasn’t noticed any indication of unauthorized activity on any Adobe ID involved in the incident, you definitely want to change the passwords for any accounts that shared the same password with your Adobe ID.



