
[Spoiler Alert] We’re about to dive deep into Mr. Robot episode 8 (eps3.7dont-delete-me.ko). While this series focuses on technical elements in the show, at times, it can’t help but spoil narrative too. Don’t continue until you’ve watched the episode.
I’m not too masculine to admit it … this week’s episode had this information security (InfoSec) geek tearing up.
LATEST IN A SERIES: Corey Nachreiner, CTO at Seattle-based WatchGuard Technologies, is reviewing episodes of Mr. Robot on GeekWire. The show airs on USA Network on Wednesdays at 10 p.m. Join the conversation on Twitter using #MrRobotRewind, and follow Corey @SecAdept.
Wednesday’s Mr. Robot episode was less about hacks and plot development, and more about building a character journey — specifically, Elliot’s. There were zero hacks in the episode, and meager computer time. While this fact did make for one of the most beautiful and redeeming character arcs, it does make it hard for this Mr. Robot Rewind article series, which is designed to analyze the hacking accuracy of each show.
However, like Elliot, I’m no quitter (I have kids that keep me happy to be alive too). Even without hacks, there were a few interesting security-related technologies, and even hacking metaphors that we can wring out of this episode. Let’s take a look.
Deletion and destruction – backing up Trenton and Mobley
Early in the episode, you see Elliot going through two processes you’ve seen him do before; making music CDs and doing his super secure computer “wipe down” process.
First, while talking about deletion in his head, Elliot takes his folders on Trenton and Mobley and adds them to his “music CD collection.” You probably remember Elliot’s ingenious music CD collection from Season 1. Like a weird “serial hacker,” Elliot seems to enjoy keeping some memento of the data or evidence about people he’s hacked (and remember, he admits he hacks everyone, including his friends). However, keeping this data is dangerous, since it constitutes evidence if he’s ever caught.
However, Elliot has a great way of hiding this data in plain sight. He burns it, along with real music, to a CD, which he labels as a music album. In fact, though I never detailed this process in my Rewind articles (I personally missed it the first time), in the past you’ve seen Elliot use a real program called DeepSound to hide this data on the music CDs.
If you haven’t heard of it, DeepSound is a steganography program that hides data in music. The CDs Elliot burned only appear to contain musical tracks on the surface. However, using this program, Elliot could extract the files he’s hidden within each track whenever he wants. If authorities ever arrested Elliot and found his “music” collection, even if they checked it, they would only find music.
Anyway, the reason I remind you of this smart process is because we do see Elliot make musically labeled CDs for both Trenton and Mobley this episode, but he seems to forget his steganography process. During the scene, Elliot makes a CD titled “Bruce Springsteen Magic” for Trenton (Shama Biswas), and “DJ Mobley” for Mobley (Sunil Markesh). While everything he does from his Linux Mint machine is totally technically accurate, we never see the DeepSound program. In fact, he doesn’t even add music to the CD as well. He simply burns the files to a CD normally.

I found this a bit strange since it could potentially come back to haunt Elliot later. Now, if authorities found his CD collection, these two are unprotected and could tip someone off that the CDs are more than they appear to be. They could even look harder at the discs that are protected with steganography, and perhaps find his other hidden files. I’m not sure if the showrunners simply chose to leave out DeepSound references as a pacing choice, or if this was an intentional mistake by Elliot they plan to use later. In any case, while this CD creation process might have looked similar to what you’ve seen him do in the past, know that he seems to have missed a big step, and did not hide those files well on his musically labeled CDs.
After making the CDs, Elliot also goes through a second process we’ve seen before; his super secure, yet destructive, wipe down process. This is where he essentially destroys many aspects of his computer. You’ve seen Elliot and Fsociety do these wipe downs before, and they make technical sense (even if some aspects are overly paranoid).
For instance, we’ve discussed before that simply deleting a file from your hard drive isn’t going to eliminate it immediately. Instead, your operating system has essentially just removed its reference to that file. For the file to really be gone, your computer has to overwrite all the different sectors on your hard drive where the file was actually stored. That’s why when Elliot really wants to “securely” delete something, he uses the shred command, which literally overwrites a file repeatedly to ensure it’s gone. During Elliot’s wipe down process, he takes the extra step of drilling his hard drive to make it even harder to recover data from.

This whole process makes sense if you are a paranoid, criminal hacker. That said, a good “shred,” with many overwrite passes probably would have done the job without the need to physically destroy the hard drive.
You might’ve also noticed Elliot snap his computer RAM. On the surface, this might seem less necessary, even to a technical person. Computer RAM, after all, is volatile memory, which means it loses its data once you remove power. However, there’s actually a good reason for this too. RAM, while volatile, takes a little bit of time (seconds, milliseconds) to forget what it stored. However, researchers recently found that if you freeze RAM, this “data remanence” lasts longer. At super low temperatures, volatile RAM might retain its memory for a few minutes without power. This leads to what security researchers called a cold boot attack, where attackers recover important and useful information from your RAM, even after your computer powers off (here are a few references). Now, this attack still requires the attacker to cool the memory while your computer is still on and the attacker only has a few minutes to recover data, but it’s possible. So, you can see why Elliot might want to destroy it.
The rest of Elliot’s actions — removing certain chips and nuking them — have equally plausible technical rationale, but are still a bit overly paranoid. I’m guessing he might have removed a network Ethernet chip to destroy this computer’s hardware address (MAC address), and he may have also wanted to destroy any other volatile memory locations on the motherboard itself (like the BIOS chip). Frankly, there’s not a lot there worth hiding.
In the end, however, Elliot’s pointed destruction of all the data storage aspects of a computer makes good technical sense for a criminal hacker with really strong OpSec.
A Kid’s Social Engineering Saved Elliot’s Life
[Major spoiler] The bulk of this episodes was not at all about hacking, but a touching story of redemption about how Trenton’s little brother, Mohammed, saved Elliot from committing suicide. Ironically, however, I think Elliot got hacked by a kid.
During this long sequence of scenes, Mohammed tries to get Elliot to take him to a movie. Elliot refuses because he’s got an important thing to do (go back to the beach and OD on morphine). However, when Elliot brings Mohammed home, his parents are gone and he appears locked out. As you know, this is how Mohammed finally convinces Elliot to take him to a movie, which later leads to a beautiful scene where Elliot sees some things in a new light at a mosque.
After that, Elliot returns Mohammed home again, where they have more touching interaction at the doorstep. However, Elliot also learns that Mohammed had the keys to get in the whole time. He had conned—or socially engineered—Elliot into that movie, and ultimately all the interactions that made him realize he has reasons to live. The student becomes the hacker master.
Proton Secure Email
In the final scene of this episode, we do get a few more accurate technical shout-outs. First, we see Elliot login to ProtonMail.

If you haven’t heard of it, ProtonMail is a really secure and encrypted email service. Normal email isn’t encrypted and is relatively easy to intercept online. You can find plenty of tools, like PGP, that can encrypt normal email, but they’re harder to use for the everyday person. ProtonMail, on the other hand, is free and easy. It offers very secure, end-to-end email encryption, and even allows anonymous accounts. This little detail is a nice, and technically accurate, touch.
One other aside … ProtonMail is actually created by researchers at CERN, a European nuclear research organization. You know CERN for creating the world’s largest particle accelerator, the Large Hadron Collider. If you’ve kept up with this article series, you know that a device whiterose visited in the season premiere looked very similar to a large particle accelerator. We still don’t know for sure what that device was, and it may not relate to this scene at all, but I just found this to be an interesting coincidence.
Trenton’s Email Reveals the Undo Button
Logging onto ProtonMail was just a way for us to get to the final reveal and cliffhanger from this episode —Trenton’s email. Turns out the person Trenton trusts was Elliot. In the final scene, Elliot opens her email, and you see the entire thing, which I’ve shared below.
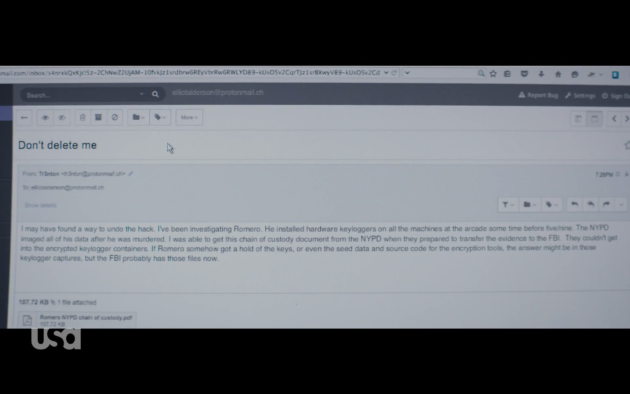
Trenton felt she had found a way that Fsociety might undo the entire 5/9 hack, which encrypted all of E Corps financial records. This email reveals how. Apparently, Trenton was investigating Romero—the OG Fsociety hacker who was shot last season. She probably did so in order to monitor how much the New York Police might be learning about Fsociety after Romero’s death (whether or not they stumbled onto any evidence that would give others away).
Through this research, she learned that Romero had installed hardware keyloggers on all the Fsociety computers at the arcade hideout. A hardware keylogger is small a device you put between a keyboard and computer, which captures and stores every keystroke typed onto that computer (these KeyGrabbers are good examples). Even though the Fsociety team had “wiped down” all the computers in the arcade (similar to what Elliot did in this episode), hardware keyloggers are small enough that Romero may have subtly removed them during that process.
So why are those keyloggers relevant? If Fsociety built the entire 5/9 attack and malware at the arcade, it is possible that those keyloggers contain something that might help disclose the encryption key necessary to recover all of E Corp’s records. Specifically, Darlene was responsible for writing the malware that encrypted all the files, and deleted the encryption key afterward. If the keyloggers caught her writing that source, then they may be able to retrieve the keys necessary to recover the data, and reverse 5/9.
If you remember, this confirms a prediction I’ve had since the first season of the show. In my Rewind articles about the season 1 finale, I mentioned how weird I thought it was that the showrunners “encrypted” E Corp’s data rather than deleting it. Ever since then, I’ve been predicting that E Corp’s data would make a comeback somehow, including in my predictions for this season (prediction 2). Trenton’s email suggests that this prediction might come true!
Right now, Romero’s encrypted keyloggers are sitting in evidence storage at some NYPD (or maybe FBI) facility. Elliot needs to find out how to hack his way into a secure evidence location and how to get the password necessary to access Romero’s encrypted keyloggers. I’ve read that the showrunners promise at least one more complex hack this season. I predict that hack will be on the NYPD.
Easter Eggs and odds ‘n’ ends
Though it was a hack-light episode, the Mr. Robot ARG team still hid a few surprises here and there:
- If you’ve followed past episode Easter eggs, you might remember the Red Wheelbarrow BBQ web site. Visiting that fake site, you’ll notice it appears to be “hacked” with a calling card left on the front page. There’s a fun little message on that calling card (from Elliot… Darlene?) painting some white roses red.
- At the beginning of the episode, you see Elliot reading a Vox article about his lost friends, who have been set up to appear like Iranian hacktivists. The whoismrrobot site has posted a link where you can peruse the full article.
- The big reveal this episode was Trenton’s email. Would you like your own copy? You see her email address during that shot. Why not email it and see what happens?
- Finally, the show’s deletion-related title played a big role this week. It has obvious relevance to the way Elliot deleted data and destroyed his computer, but the theme played out throughout other aspects of the episode. Digital data (files, encryption keys, etc.) can sometimes come back if not deleted properly. It was also fun seeing Elliot try to delete Mr. Robot by dumping his jacket, only to see it return later.
Learning from Mr. Robot: Make sure to destroy your data
In an episode about deletion, the best practical security takeaway is to adopt at least some of Elliot’s paranoia about data destruction. If you ever get rid of an old computer, I don’t think you need to pull out the power drill or nuke all your microchips. However, realize that remnants of data on your storage drive still stick around for a bit if you delete data normally. Before you throw away or sell a computer with a hard drive, be sure to use various utilities (like Shred) to securely wipe all your data for good, so that even forensic data recovery programs can’t salvage it. Otherwise, the next owner might gain access to your files, personal photos and more. If you work for a business, do know there are services for hardware data destruction, which will take your computers and hard drives and wipe them clean, even using physically destructive methods like Elliot’s.
So, that’s it for another relatively hack-less episode. However, it’s likely this trend will turn. I think the final two episodes of the season will explode with hacks. Be sure to join me next week with another Mr. Robot Rewind. Meanwhile, I’d love to hear your thoughts and comments below.


