
[Spoiler Alert] If you haven’t seen the latest episode of Mr. Robot yet, you may want to come back to read this later. While this column focuses on the technical aspects of the show, it may reveal some surprises from the episode. Consider yourself warned!
LATEST IN A SERIES: Corey Nachreiner, CTO at Seattle-based WatchGuard Technologies, is reviewing episodes of Mr. Robot on GeekWire. The show airs on USA Network on Wednesdays at 10 p.m. Join the conversation on Twitter using #MrRobotRewind, and follow Corey @SecAdept.
What do you write about when there are no hacks in the show you are analyzing for its technical hacking accuracy? You talk about the bat crap insane CTO choking out his competition’s wife… OMG, right?Seriously though, if you haven’t been with us from the beginning, this article series analyzes the technical accuracy in USA Network’s popular and well-reviewed cyber thriller, Mr. Robot. Unlike last week’s episode, which covered a cyber prison break hacking bonanza, this week mostly drove the narrative of the show. However, there were a few technical moments and descriptions of hacks that we can scrutinize. So let’s jump in.
Viewing source on 2600.com
The first real technical scene comes after Elliot’s boss says, “find someone you can be your honest self with.” This gets Elliot thinking about source code, which is how he first learned to code HTML. He’d find a site he liked, view source, and change a few things.
While every hacker has their own “origin” story, I’d bet many started in a similar manner. Many learned to code informally. For instance, I learned from my old “Trash 80” or TRS-80. This old computer booted straight to a BASIC prompt. Though you could buy games for it, my dad didn’t approve and I had no money. If I wanted to play a game, I had to painstakingly type out code, which I’d find in a magazine. Worse yet, my game would disappear as soon as I turned off the computer (since I didn’t own a tape drive). Though this process seemed tedious at the time, it started me on my path to coding. It also allowed me to see how others solved problems within their code, which I could then reuse in my own programs.
Elliot’s soliloquy about viewing source rings true to me as a hacker’s view of the world. They want to know how things work, and how people work. I also believe folks who learn to program informally can become the best hackers. They tend to look at problems from outside of the confines of a formal process, which can provide the freedom to try weird things that others wouldn’t.
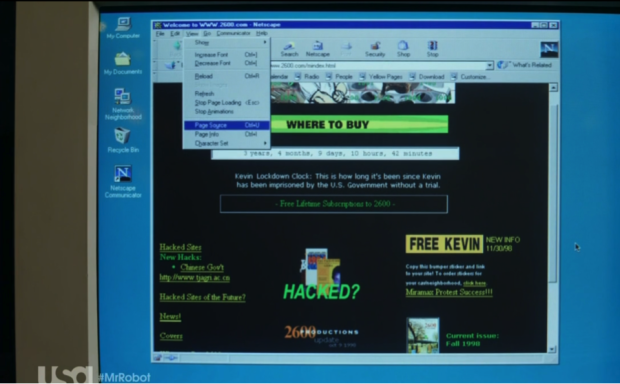
While we’re on this scene, let’s look closely at the website Elliot is ripping — 2600.com. If you haven’t heard of it, 2600: The Hacker’s Quarterly was an e-zine about phreaking and hacking, which came out in the 80s and is still around today. If you’re wondering, 2600 is not a reference to the Atari, but to a 2600Hz tone that would give you operator privileges on the old school tone-based phone system. Anyway, the use of 2600 is a fun Easter egg for security nerds. In fact, if you compare the screenshot above to what the real site looked like circa 1999, you’ll see the show is spot on—Kevin Mitnick references and all.
Dark Army’s Cisco gets rooted
In Episode 7, Fsociety desperately tries to get back in touch with the Dark Army, in hopes of rekindling their Steel Mountain data destruction hack. We don’t actually “see” any hacking, but we hear that Darlene has pwned Cisco’s computer in order to impersonate him and contact someone called White Rose. At one point, Cisco says something like, “you rooted my box, got the IP, and joined their channel with my handle.”
Though it’s light on details, this description sounds consistent with how someone might impersonate you on IRC. IRC hacking is pretty common. In fact, back when botnets were less sophisticated, good guy hackers could packet sniff infected computer traffic, find the IRC server IP, channel, and password the bot used. They’d use that data to connect to the attacker’s command and control (C&C) server to spy and take over their botnet. In short, IRC hacks between hackers are par for the course.
A few other tech wins in this hack-free episode
- Early in the episode, we learned a month has gone by since Shayla’s death. This means there has been a trojan in Allsafe’s network (remember the CD?) for over a month, and Allsafe still doesn’t know about it. This is true to life. According to Poneman research, it takes organizations on average over 80 days to learn they’ve been breached by an attack. Today’s sophisticated malware is more silent and persistent than ever before.
- I haven’t commented on the Fsociety’s masked-man videos yet, but for anyone that has seen an Anonymous video from the folks who’ve popularized the Guy Fawkes mask, you know these are portrayed fairly accurately.
- What’s with Elliot burning all his favorite hacks and digital mementos on CDR? On one hand, this feels like something some hackers might do; they can have egos, and want proof of their work. However, Elliot has pretty good OpSec, and saving evidence of his crimes, protected only by weak mislabeling, seems uncharacteristic of a hacker of his caliber. I hope he’s at least encrypting the data. (I also don’t buy some of the musical choices for his labels. The Cure and Tool fit his personality, but Van Halen?)

- In one scene, Darlene tries to get the other female Fsociety hacker to rejoin the crew. The Iranian hacker talks about the motivations for the other hackers in the group. While these motivations may not cover all the intentions of today’s real world attackers, it is true that every hacker has a reason, and knowing those motivations can be a key to your defense.
A prediction
I think Elliot’s dog might become his downfall. There’s a very short scene where Elliot takes his dog to the vet, and finds that it has been micro-chipped. Animal microchips are based on the same RFID technology I talked about in an earlier article. Anyone can scan for and read RFID microchips, if they’re not sufficiently protected. I’m guessing the microchip will play some part in a future episode—perhaps as a means to track Elliot.
In closing
Although this episode was relatively hack-free, it still accurately represented how technology can be used for and against us. If you only take away one thing this week, it should be to remain aware of what your online presence reveals about who you really are. Don’t let hackers view your “source.”
Let us know what you think in the comments section, and join me next week for another Mr. Robot Rewind.


